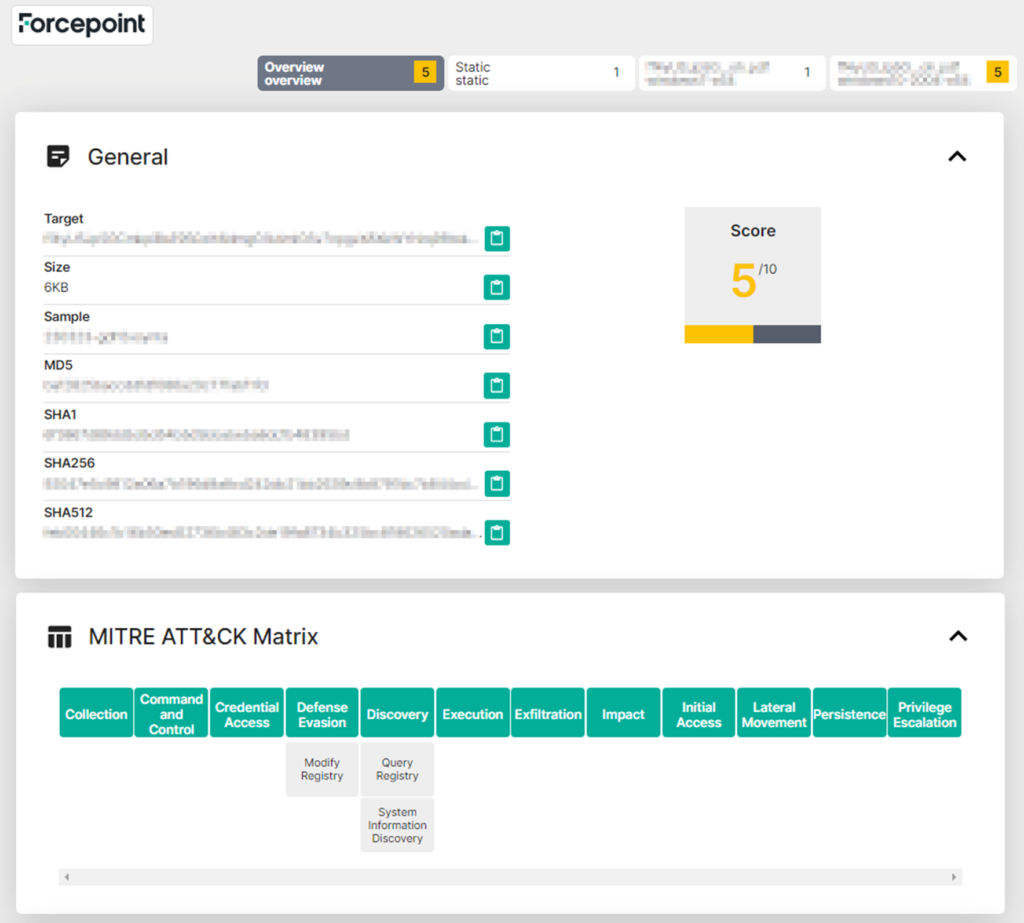
Enhance security posture with Forcepoint Advanced Malware Detection and Protection (AMDP)
Organizations understand these risks and are taking steps to mitigate their exposure and withstand the storm. The question is, what type of storm are they preparing for, a spring shower or a hurricane? Organizations preparing for a worst-case scenario will upgrade and bolster their defenses and may upgrade from a firewall to Next-Generation Firewall (NGFW), […]